Archive
A Review of the Grizzly Steppe (Russian Hacking) Report
I, like many, have heard the stories that the Russians hacked into sensitive applications/servers in an effort to compromise the US elections. That is a bold statement and if true, may justify the actions recently taken by the Obama administration. So it was with keen interest that I rushed to read the findings from the Joint Analysis Report (JAR-16-20296) between DHS and the FBI to see what evidence they had to substantiate these claims.
The full report may be found here:

The report makes the following claims:
“This document provides technical details regarding the tools and infrastructure used by the Russian civilian and military intelligence Services (RIS) to compromise and exploit networks and endpoints associated with the U.S. election…”
“Previous JARs have not attributed malicious cyber activity to specific countries or threat actors. However, public attribution of these activities to RIS is supported by technical indicators from the U.S. Intelligence Community, DHS, FBI, the private sector, and other entities.”
Based on this information the US felt like it had the smoking gun and definitive proof of the following:
- The Who – the Russians were behind the attack
- The Why – to affect the US elections in order to guide the outcome
With this information in hand, I continued reading to now learn about:
- The How – how the attacks were performed
- The Proof – the evidence to substantiate Who, Why, and How
The report describes the “How” in a two pronged attack as follows:
Hack #1 – Casting the Phish Net…

1. A general spearphishing attack was sent to more than 1,000 people which included (in addition to others) several people from the U.S. Government.
Note: The number “1,000” is very specific so it seems like the government has some knowledge of the recipients – but they stop short of specifying if that 1,000 was directed at a particular party or not. I would think that would be important to know if the purpose of the attack was to affect the US election.
2. The attack led to one person from a particular U.S. political party falling prey to the attack and opening an attachment containing malware. This led to a chain of events where the malware was able to:
- Establish persistence on a “political party system”
- “Escalate privileges”
- “Enumerate Active Directory accounts”
- “Exfiltrate email from several accounts through encrypted connections back through operational infrastructure”
Note: This all sounds really impressive, but what does it all mean? If you remove all the jargon (enumerate, exfiltrate, etc.) and put this in layman’s terms, it sounds like the following occurred:
- Someone installed malware on their PC when they opened a file that they shouldn’t have
- Somehow the malware was able to gain privileged access to Active Directory
- The malware was able to perform a search against Active Directory
- The results of the search returned several email accounts
With this information on mind, there are a few things I am curious about.
First, the malware is only able to impersonate the user on the operating system on which it was installed. I’m not sure how a “normal user” can have escalated privileges in Active Directory unless that user is an administrator with escalated privileges (which brings up a whole different conversation about administrators knowing better). So I am curious how the malware was able to “escalate privileges” on its own.
Second, if the user (hence the malware) was not an administrator and they were able to perform an unauthorized search against Active Directory, then that indicates that Active Directory authorization and/or limitations were not configured properly. It has been my experience that Active Directory is (by default) pretty well locked down. Is it possible that the default settings were “relaxed” a bit and therefore may have opened up a hole?
Finally, would I really need “escalated privileges” just to troll email accounts? Couldn’t I simply scan the Outlook address book to obtain this information? It seems like the approach described in the report would take a lot of effort to code and would have a limited chance of success. Wouldn’t the malware have to land on an administrator’s computer for this approach to work?
3. Either way, the end result was that APT29 was able to get a list of email addresses from Active Directory.
Fast forward almost a year later (summer 2015 to spring 2016) and this takes us to the second part of our story.
Hack #2 – Hooking the Phish…

1. In the second hack, a targeted spearphishing attack was launched against the same political party that was compromised in the first attack.
Note: It should be noted that while the first attach was general (casting a net if you will), the second attack was targeted at a certain set of people using specific information to more easily trick those people. While the report doesn’t specifically say this, it is assumed that the attack targeted those email addresses that were obtained from the first attack.
Does this indicate that the political party in question was targeted because the end goal was to affect the election? If so, then this attack was planned almost a year in advance when we really didn’t have a clear picture as to who the candidates would be from either party. Were the Russians hedging their bets in case a certain party (or a certain candidate) was found to be leading? It seems more plausible that the second attack was launched more against a certain set of users more as a target of opportunity than anything else.
2. This spearphishing attack tricked multiple people into “changing their passwords through a fake webmail domain hosted by APT28”.
3. Upon initial login, APT28 was able to obtain the “real” credentials of users associated with the political party in question.
4. With these credentials in hand, APT28 was able to log into the real email server and access content (emails, attachments, etc.). The report goes on to say that this information was subsequently “leaked to the press and publicly disclosed.”
Where’s the Smoking Gun?
While the report is somewhat interesting, it does not provide the “smoking gun” that was anticipated. The report does provide a list of 48 hacker names of which APT28 and APT29 are included. The title of the table is “Reported Russian Military and Civilian Intelligence Services (RIS)” but there is nothing more than that to introduce the table and tell us anything about the names contained in the table. Am I supposed to jump to the conclusion that because APT28 and APT29 are listed that this is definitive proof that:
- they are the ones behind these attacks
- no one else has attempted to use these names as their hacking alias
- they specifically targeted a particular political party
- their intent was to affect the US election
- and most importantly, they are “state sponsored”
The last item is one of the most important as the administration has chosen to take action against Russia (the state) as if they sanctioned the attacks. If that is true then the need for a smoking gun becomes infinitely more important and that information is simply not provided. Going back to a statement made early on in the report,
“Previous JARs have not attributed malicious cyber activity to specific countries or threat actors. However, public attribution of these activities to RIS is supported by technical indicators from the U.S. Intelligence Community, DHS, FBI, the private sector, and other entities.”
the government has made it clear that it is stepping outside of normal protocol by publicly naming the attacker in the JAR. But they don’t provide any information to back up their claim. Nor is there anything specifically that indicates that this had anything to do with an attempt to affect the outcome of the US election; in fact, the information presented may lead one to believe the contrary.
In general, the report lacks information and forces us to accept the government’s assertion of the Who (the Russians) and the Why (to affect the election) without providing the Proof. Maybe the government has more information that they are not sharing, but to ask me to simply trust without verifying is asking me to trust too much.
The Dimishing Non-Digital World (or How to get Outed by a Photo Booth)
 I recently attended a high school reunion where a major draw involved the use of a photo booth. You remember photo booths, right? Kiosks where one or more people hide behind a curtain and take pictures of themselves in all sorts of poses. At the end of the session, the kiosk spits out copies of the pictures much to the chagrin of those who aren’t quite as photogenic as they initially thought they were. In our case, reunion attendees were treated to an assortment of funny hats, glasses, and mustaches before entering the booth. They posed with silly expressions, engaged in silly activities, and in some cases even took silly actions to the extreme (I will leave that to your own imagination).
I recently attended a high school reunion where a major draw involved the use of a photo booth. You remember photo booths, right? Kiosks where one or more people hide behind a curtain and take pictures of themselves in all sorts of poses. At the end of the session, the kiosk spits out copies of the pictures much to the chagrin of those who aren’t quite as photogenic as they initially thought they were. In our case, reunion attendees were treated to an assortment of funny hats, glasses, and mustaches before entering the booth. They posed with silly expressions, engaged in silly activities, and in some cases even took silly actions to the extreme (I will leave that to your own imagination).
The point I am trying to make is that once the curtain was closed and the camera light came on people began performing in ways that would be considered unheard of in other settings. Adults who mere minutes before were prim and proper were now raving exhibitionists behind the privacy of a thin veil of cloth. When the curtain was once again opened, they returned to their “normal” behavior and giggled as they left the booth with memories in hand.
So why the sudden change? How did a thin piece of cloth make any difference as to how they acted? The difference was not the curtain, the difference stemmed from their perception of privacy and the context of the situation. People tend to act differently in settings where they feel their actions are private and when the context of the situation is known, they oftentimes let their guard down and act more naturally (or more boldly as the case may be). Just think about Congressman Weiner and his Twitter outing, Alec Baldwin and his fatherly advice to his daughter, or even conversations that you may have had over email, chat, or text when you didn’t think anyone was looking. When people feel more secure in their settings (privacy) and know the rules by which to play (context), they oftentimes act in totally different ways.
The problem with this behavior in a digital society is that you are never truely off the grid and it is all too easy for things to be taken out of context when information is shared inadvertantly. In our current digital society privacy is a facade as few companies take privacy seriously and there are fewer online places where your information is truly secure. Unfortunately, that can also be said of our offline world as more and more of it is becomming digitized as well.
Even within the sacred confines of a photo booth our privacy is not really private at all. Ironically photo booths now take digital photos which are then stored on the kiosk’s computer hard drive. While this expidites the printing process, the possability of those photos being shared with unintended parties is very real. At least that is what I observed shortly after the reunion when pictures from the photo booth began appearing on Facebook. At first I thought that attendees were scanning their own photos and posting them. This thought was immediately dismissed when I saw my own pictures start to appear.
From what I can surmise, the operator of the photo booth provided digital copies of everyone’s photos to one of the reunion committee members who took it upon themselves to post the pictures to Facebook. I am not going to get into the legal, moral, or ethical issues behind this action, but suffice to say, no notice was posted and no permission was granted. Now, I truly believe that those involved had the best intentions of the reunion attendees in mind, but the problem is that they did not have the right to make that decision on their own.
 Intersection cameras, movies on demand (on any device), automobiles that act as WIFI hot spots, Internet connected scales, and yes photo booths – these are only a few examples of how every aspect of our life is becoming affected (or even consumed) by digitalization. All of that content is finding its way into the hands of people who may have good intentions, but who do not understand the ramifications that disclosure of such information may have. As such, they may not take the same care that you or I might take with our own information and may share it with others – all under the guise of good intentions.
Intersection cameras, movies on demand (on any device), automobiles that act as WIFI hot spots, Internet connected scales, and yes photo booths – these are only a few examples of how every aspect of our life is becoming affected (or even consumed) by digitalization. All of that content is finding its way into the hands of people who may have good intentions, but who do not understand the ramifications that disclosure of such information may have. As such, they may not take the same care that you or I might take with our own information and may share it with others – all under the guise of good intentions.
So what happens to our privacy when our information falls into the hands of others? Is it even possible to assume that they have our best intentions in mind when their own companies make money by selling our data to the highest bidder? Can we assume that the context in which we operated is even valid when it may simply be a ruse to get us to let our guards down? Like Rip Van Winkle awaking from his 20 year slumber only to find a world that he no longer recognizes, we too must take care that we resist our own apethetical slumber or we too will wake up to a world we no longer recognize.
A New Generation of Indentured Servitude
Your digital identity is comprised of information that you volunteer about yourself and information that is observed about you as you simply participate in life. You can (somewhat) control the personal data that you share with others, but have you ever wondered about the type of information that is gathered about you, how long it is retained, and how it is used?
A friend of mine introduced me to a video that provides insight into these questions. It contains an interesting perspective on how your digital identity is comprised, collected and used.
It is interesting to note that almost four years of our lives is owned by someone else – and we willingly give it away. Does that make us indentured servants to those vendors who provide us “free services” in return?
The speaker makes another interesting comment at the end of the video,
The global Internet becomes the personal Internet and information ceases to be information at all.
I am not entirely sure that I agree with that statement; I guess it depends on who it is being made about. Unless we (the ones who generate the data) benefit in the form of better applications, streamlined experiences, or potentially even financial returns, then I don’t see it becoming a “personal Internet” at all.
In our current form of indentured servitude, we continue to give away pieces of our freedom in return for very little.
It is time to turn the model around.
How Well Do Your Vendors Really Know You?
How well do our vendors know us? I mean, how well do they really know us? And how much do they care?
They collect countless data points about us through direct or indirect activity. They spend a lot of money buying lists containing all sorts of information about “people like us”, but what are they actually doing with all that information? Are they using it to create products geared towards our needs? Are they using it to make our shopping experience any better? Are they using it to make us feel special?
Are they even using it at all?
Based on one experience, It seems like some companies (some big name companies) just aren’t getting it.
Here’s my story…
You might consider me a coffee fanatic – the stronger and the hotter the better. I will wake up first thing in the morning and make a 12 cup pot of Cuban  coffee (one of my favorites) with the intention of drinking every last drop. But, as with the best laid schemes of mice and men, I typically throw some of that coffee away (I know, sacrilegious). So, when a few years back vendors started producing one cup coffee makers with the pods, I figured what the heck, it is still cheaper and easier than Starbucks. So I figured I would make the switch; but which one?
coffee (one of my favorites) with the intention of drinking every last drop. But, as with the best laid schemes of mice and men, I typically throw some of that coffee away (I know, sacrilegious). So, when a few years back vendors started producing one cup coffee makers with the pods, I figured what the heck, it is still cheaper and easier than Starbucks. So I figured I would make the switch; but which one?
I researched, I asked friends, I tested, I priced, I researched some more and I ended up with a Tassimo brewer from Bosch (a division of Kraft Foods). This coffee maker was reasonably priced and it did so much more than the competition. Expresso, cappuccino, latte, hot chocolate, tea – I could make it all with this little gem. I just knew I had made the best choice and my coffee wasting days were behind me. I was so satisfied with the product that I became the Tassimo poster child. I registered my system on the Tassimo Web site and gave Bosch my personal information (something I rarely do). I told all my K-Cupping friends about my state of the art coffee making mecca. I celebrated the Tassimo robot commercials on TV. Heck, I became a one man Tassimo advertisement. You could consider me the epitome of a loyal Tassimo customer.
Unfortunately, over the past year or so I found that Tassimo coffees are getting harder and harder to find in retail outlets. Apparently Keurig made better agreements with coffee manufacturers like Starbucks than Kraft did and the availability of my dream coffee started waning. But I was not to be deterred, Tassimo had a Web site, right? So, I started ordering my coffee direct. This satisfied my need for awhile, at least until the choices became fewer and everything started being put on back order (especially my wife’s favorite, caramel macchiato). But I stuck with them – still believing in my choice of brewers.
I mention this because I have put more into my Tassimo relationship than Bosch has. So, when I received the following email from Bosch telling me that they appreciated my business and were inviting me to a “Customer Appreciation Event”, I felt that they finally started recognizing my investment.
Based on the email, I could save $10, $15 or $25 – depending on how much additional loyalty I was willing to demonstrate . Apparently “loyalty” is measured by the number of dollars I am willing to spend now, not what I have already spent in the past. Nor is it measured by the fact that I have continued to stick with them even though half the time the items I want are on back order or that I continue to shop with them even though their merchandise has mysteriously disappeared from retail shelves. I didn’t respond right away, but the email did make me feel somewhat “special”.
Three days later I received an email with the subject of:
LAST DAY to Shop and Save $10, $15 or $25
Apparently Bosch appreciated me, but only during the three days of the sales event, itself. Is that appreciation? Hardly.
But, being the price conscious person that I am, I bit. I went to the web site and put in my order for over $100 dollars of merchandise to get the maximum discount (of which $75 worth of product was back ordered). Sigh….
Did Bosch consult their records of my buying history to help me make my purchase? Did they steer me towards those products that I have faithfully purchased in the past? Did they give me a whole-hearted apology for my products being on back order (for the umpteenth-millionth time)? Did they in any way make me feel “appreciated” in this transaction? Hardly. In fact, the whole experience has had the opposite effect. Instead of feeling appreciated, I feel like I was being used to help Bosch reach a sales quota.
Unfortunately, the sales process has become a contentious relationship between the customer and the vendor. Customers are wary of being taken advantage of by vendors who are only out to sell (caveat emptor, right?). They feel that vendors are only out to take advantage of them, so they will do whatever they can to take advantage of the situation first. Unfortunately vendors who actually do care about their customers are all too often lumped into the same category as predatory ones (have you been to a used car lot lately).
The trust between the customer and the vendor is all but gone.
The fact of the matter is that it doesn’t have to be that way. Customers can be fiercely loyal to brands (just ask Apple, Levis, or Budweiser) and all that it takes is for the vendor to show an ounce of loyalty back. It doesn’t take much, just enough to make customers feel like they are valued. Just enough to make them feel like they have a say in the sales conversation, just enough to make them feel like they are truly ‘special’.
Is that too much to ask for?
A word of advice to vendors, ‘they don’t care how much you know until they know how much you care’.
How much do you really care about us?
Trust in Me
Trust in me, I’m the social media vendor providing this FREE service because I want to make you happy. I know that all of this infrastructure and the thousands of employees I have working for me are costing a small fortune, but I do this because I care …. I care about YOU!
Trust in me, I’m the software development company who develops these FREE applications because we are looking out for you. We know that you need something entertaining to do or something informative to occupy your time. We ask you questions about your preferences so that we can customize the software for YOU. That’s the only reason, trust us.
Trust in me, I’m a one man developer operating out of my house creating these FREE applications so that you don’t have to pay for the premium ones. I have no visions of grandeur for myself. I have no dreams of making money for myself, I am doing this for you!
REALLY? No catches at all? Awesome, where do I sign up?
I learned a long time ago that there is no such thing as a free lunch, yet people continue to be duped into believing lies to the contrary. Let me be clear,
Privacy is an illusion in our current social media landscape. Period.
If you think that these FREE services are free then think again; they are anything but. In fact, social media companies and application developers are making money off of the very things that are most precious to you – they are making money by selling information about you and your loved ones. Whether they are selling this information directly or indirectly through advertising, these entities are collecting thousands of pages of information about you – enough to fill volumes of books. Don’t believe me, read Kim Cameron’s article, 24 Year Old Student Lights Match: Europe Versus Facebook.
Your preferences, your habits, your activity – essentially your life – is meticulously tracked by social media sites and used to predict your behavior. With this information in hand, they seek out those who are looking to target those with this behavior or are willing to pay to gain access to these people. It is a well-known fact that social media sites may know more about you than your own family members do, but social media is not the only culprit. “Real world” businesses have been tracking your behavior for years and are just as savvy as social media sites (see How Target Figured Out A Teen Girl Was Pregnant Before Her Father Did). The amount and types of data associated with social media sites is much greater than that obtained in brick and mortar stores as it is more plentiful, easier to gather, easier to store, and easier to analyze.
In George Orwell’s book, 1984, we were worried about a Big Brother that we feel never came. In reality, however, he came and brought his whole family with him and they are all watching us. Get used to it, or take the steps necessary to protect your information assets the same way you protect the money in your bank or your legal documents.
Last month, I wrote a blog entry entitled Which Line Do You Want To Be In? in which I stated that people are
willing to trade important things in life for short term gain
Unfortunately when convenience and privacy are at odds with each other, people tend to throw privacy out the window in trade for convenience. Are these people oblivious or do they simply feel that they have no choice. Have they made a conscious decision or are they simply uneducated to the risks associated with privacy breaches? I tend to believe that most people are too trusting and do not know (or simply do not understand) what information is collected about them and what happens when their information is inadvertently shared. You can classify these people based on age and/or knowledge of technology as follows:
- Typical Kids – who do not yet understand privacy implications
- Typical Adults – who may understand privacy, but don’t understand technology and how it can affect their privacy
- Tech-Savvy Adults – who understand privacy AND take an active role in protecting themselves on social media sites
For those of you who fall in the third category, I know that I am preaching to the choir here, but unfortunately the vast majority of people do not attend the church where this message is being preached. There are still many people who have never heard the message or if they have, they simply choose to ignore it. Is it because they disagree that information is being tracked? Or is it maybe that privacy policies on most social media web sites are simply too difficult to read and/or understand and it is simply easier just to “click through” to get to the site that we want.
I once heard that marketing agencies build their message so that a person with a 7th Grade education can understand it. That is an unfortunate statement to the intelligence of the average American. Unfortunately, it is also a statement that many companies rely on when crafting their legal documents.
Suffice to say, if the price is FREE, it may be costing you dearly.
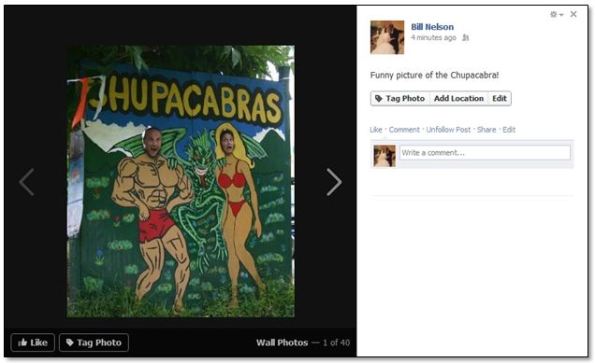
Facebook Photo Hack Bypasses Privacy Settings
Do you use Facebook? Since over 700 million people do, the odds are pretty high that you fall in this category. Are you concerned with your privacy and want control over who sees your content? Have you taken all the steps necessary to keep your private information private and feel pretty good about yourself? Well think again. While you may be taking every precaution to keep your data private, some items (such as your photos) are totally open. Still feel good about yourself? Keep reading.
Let’s say that you are on vacation and decide to take a few pictures to memorialize the trip.
You want to share your pictures, but you only want to do so with some of your closest friends (you don’t want these photos to be public). So, you select the upload photo option, point to the picture on your local computer, make sure that the Friends option is selected, and click Post.
The picture appears on your wall where only you and your friends can see it. You verify this by viewing the audience for the picture as follows:
Your friends comment and you all get a big laugh from the picture. But one of your not so close friends thinks it would be funny to show the picture to someone else – outside of your friends community – without your permission. Now, they could download the picture to their local computer and upload it somewhere else, but that takes too many steps – Facebook makes it much easier for you to be compromised.
Simply click on the image to open Facebook’s photo viewer.
Now right-click on the photo and select “Copy Image URL” from the browser menu that opens. You will have copied something like this:
If you look at the URL, you can see that this image is not hosted on Facebook’s site. Instead, it is hosted on Akamai’s site (a place where your privacy settings do not apply). By simply knowing this photo’s URL, anyone in the world can see this picture. All your “friend” has to do is share out this URL and all the time and efforts that you have taken to be private are now out the window.
Don’t believe me? Try this for yourself. Or simply click on the link above to see a picture that I have supposedly made private in Facebook.
Which Line Do You Want To Be In?
I stumbled across the following image the other day and thought it was too good not to share.
Consider the information that you share with social networking sites on a daily basis. Are you guilty of giving up your privacy in return for things that are transient? I think to some degree we all are. We have become a society that is willing to trade the important things in life for short term gain.
But it is time to ask yourself, which line do you want to be in?
Dealing with Grief in a Social Setting
We had to put our family dog down.
Princess Buttercup of Petersburg was my daughter’s first real pet and as my daughter grew so did Buttercup. For the past twelve years we celebrated life’s events and Buttercup was right there with us, every step of the way. Birthdays, holidays, even more pets; we could look back through our memories and there was my daughter’s best friend, a part of the family, celebrating right there with us. And now there is a hole in our hearts and lives where Buttercup used to live on a daily basis.
The sorrow that gripped my family was intense and each of us dealt with it in a different way; but it seemed to hit my daughter the hardest. She withdrew from the family and seemed to want to deal with the death of her friend on her own. At least that is what I thought until I saw my daughter’s Facebook status.
I read her words and they literally tore open the wound that I had so carefully closed the previous day. As I fought back the tears I suddenly realized that my daughter had not withdrawn, she had simply found a way to share her pain in a way that I could not and she chose to use her social network to do so.
Don’t get me wrong, I also wanted to say something about Buttercup, but I struggled to find just right words. It seemed that every carefully crafted message that I wrote was quickly dismissed as I considered each one inappropriate for one group of friends or the other. I wanted to confide in my closest friends but not share with a general audience. I wanted to post something that would honor Buttercup’s memory, but I didn’t want to deal with the awkward questions or the “I feel your pain” stories that were sure to follow as people felt obligated to respond to my post. So I simply said nothing wishing that Facebook truly had some way for me to selectively share my feelings with my closest friends. But on Facebook, you are either an open book, or you are forced to take your business elsewhere? But where? They have already cornered the market on all of my friends.
My lack of saying something made me question if I truly shared in my family’s grief. But my wife did not rush out to post either so it made me wonder if this is a generational thing. Are today’s youth able to post about every aspect of their lives while we still like to compartmentalize ours? Are the concepts of context and roles breaking down as everyone has access to the same information about you? Should your clients be privy to the same information as your family members? Does that draw them closer or push them away?
 In 2010, Mark Zukerberg declared that privacy was no longer a “social norm” and that user information should be public. This was largely based on Facebook’s observation of the types of information that people were sharing with each other. As such, Facebook modified their privacy policies and subsequently their platform to share more and more information. But there are some things that I simply don’t want to share with the entire world. So my only options are to either adopt Facebook’s open model or suppress my activity on the site. Thus far, I have chosen the later, not because it is what I want to do, it is only because it is the prudent thing to do. Some people are comfortable sharing everything with everyone, some are not. But while I was struggling with the right words to say, my daughter was saying them.
In 2010, Mark Zukerberg declared that privacy was no longer a “social norm” and that user information should be public. This was largely based on Facebook’s observation of the types of information that people were sharing with each other. As such, Facebook modified their privacy policies and subsequently their platform to share more and more information. But there are some things that I simply don’t want to share with the entire world. So my only options are to either adopt Facebook’s open model or suppress my activity on the site. Thus far, I have chosen the later, not because it is what I want to do, it is only because it is the prudent thing to do. Some people are comfortable sharing everything with everyone, some are not. But while I was struggling with the right words to say, my daughter was saying them.
What I find interesting is that there is an entire generation that has essentially become open books with both their feelings and their personal information. While older folks value their privacy, it seems like the younger ones are more open to sharing. Is this because they agree with Zuckerberg’s view on privacy? Or is it that they simply do not have a choice and they must play by someone else’s rules. I contend that it is the later and people are willing to exchange privacy for convenience in a world where they don’t have both. Facebook takes advantage of the fact that humans are social beings and the drive to be social is stronger than the drive to be private or simply careful. Most “Millennials” are OK with this and don’t give it a second thought – that is until their openness is taken advantage of and they are compromised in some way. Then they scream about how this could have happened and why they were not protected.
In the case of Buttercup’s passing, my daughter chose to play by Facebook’s rules and share her feelings with the world. Did she consciously make this choice, or did she simply use the only tool available to her express her feelings? Does she value privacy as much as us “older folks” and would she have chosen to use another conduit to share her grief if it were available? Ah, there’s the real question, but it is one that is impossible to answer until she has real alternatives to choose from. Ultimately Facebook will face more and more competition (think Google+) and some competitors will place a higher value on privacy than Facebook, but they have a lot of catching up to do. As Facebook continues to grow larger each day and as they approach an impending IPO that will put them on par with companies like General Electric, it is going to be more and more difficult for competitors to capture the intellectual capital that so many users have elected to invest in Facebook. Can competitors erode Facebook’s market share? Only time will tell, but in my opinion, it is about time.
Trust – The Missing Ingredient
I was having a conversation with friends the other day and while it may sound nerdy as hell, the topic was focused on identity. I swear (trust me) that no drinks were involved but the conversation went pretty deep, nonetheless. What is identity, how is it used, and how can it be protected? Like Aristotle and Plato before us, we modern day philosophers discussed the various aspects that make up our identity, how we can control it, and how we can selectively share it with our intended audiences. In an era when our private information has been unleashed like the proverbial opening of Pandora’s Box, how can we regain control of our identities without impacting our existing relationships or experiences?
But what about identity? What is it really, and why should you care?
When I think about identity, I think in terms of aggregation, management, and sharing. Each of these are key ingredients when it comes to users owning their own identities, but each of these can be further strengthened when we add trust to the mix. So, what is the recipe for success as it pertains to trusting identities in cyberspace? Let’s take a closer look at each of these ingredients to see.
Aggregation
My identity is the aggregation of all the things there is to know about me. One could trivialize this by saying it is simply all the discrete data elements about me (i.e. hair color, height, ssn, etc.) but in essence, it is much more. It consists of my habits, my history, my data, my relationships – basically everything that can be me and everything that can be tracked about me. Identity information is not found in a single location, it is distributed across multiple repositories but this informaiton can be aggregated into a virtual identity – which is essentially, me.
Management
When we allow someone to manage their own identity, we are allowing them to control their discrete data elements, but we are also allowing them to manage every other aspect about themselves as well. You can change your mobile number attribute (data element) when you get a new phone, or you can change your address attribute when you move. But just like you can remove the cache, history, and cookies in your browser, you should be able to maintain your privacy by removing (or hiding) your identity characteristics as well. Identity management simply means that I am able to manage those aspects of my identity that are my own.
Sharing
In real life, I have the ability to select which characteristics and/or information about myself that I want to share with each of my friends, family, co-workers or acquaintances. My work-related benefits stay private between my boss and I in the workplace. Conversely, I don’t share my family conversations within the office. Investment information stays private between my broker and I, yet I Tweet favorite quotes to the world. In essence, I selectively share information with different audiences based on the role I am playing at that time. Online personas facilitate the same selective sharing within the social web similar to our interations in the real world. I may take on a different persona as I interact in the virtual world and elect to share different information with each audience based on where I elect to use that persona. This also means that I can act anonymously if I so choose (which is similar to going ‘incognito’ in your browser).
Trust
Sharing data with others fulfills my desire to communicate information about me to you, but just like in real life it is totally your option to accept the validity of that information or not. To take the sharing to the next level (and address a major need on the Internet today), we need to have some method of trusting the information that we receive. Trust is transient (it changes), contextual (it is based on the situation), and 100% given by the receiving party – essentially they decide to trust you or not. In the real world we use driver’s licenses, passports, or referrals from friends to validate users and establish trust. This is no difference in the social web except for the fact that we are not seeing each other face to face and do not have the ability to provide a driver’s license as proof of identity. Hence the need for another method.
If the ingredients in the identity cake are aggregation, management and sharing, then validation is the icing on the cake; not the cake itself. While each of these ingredients are key in making the perfect cake, leaving trust out of the mix is kind of like leaving salt out of the recipe. Trust simply brings out the flavor and without it, the cake is way too bland!
Facebook’s Trolling for Keywords
I posted a status to Facebook that included the words “Sea World” and all of a sudden I received a recommended page for Sea World and other Orlando theme parks in their advertisement section. Does anyone really think that Facebook isn’t parsing every post for nuggets they can glean and use for advertising purposes?
From a technical perspective, it is pretty impressive. From a privacy perspective, it is very very scary.